PRODUCT
Secure Business Connect for Seamless Remote Working
Discover the future of adaptable Secure Access management, offering an improved and safer approach to maintaining the safety of your company network.
WHAT IS IT
How Next-Generation Secure Access are Revolutionizing Digital Security

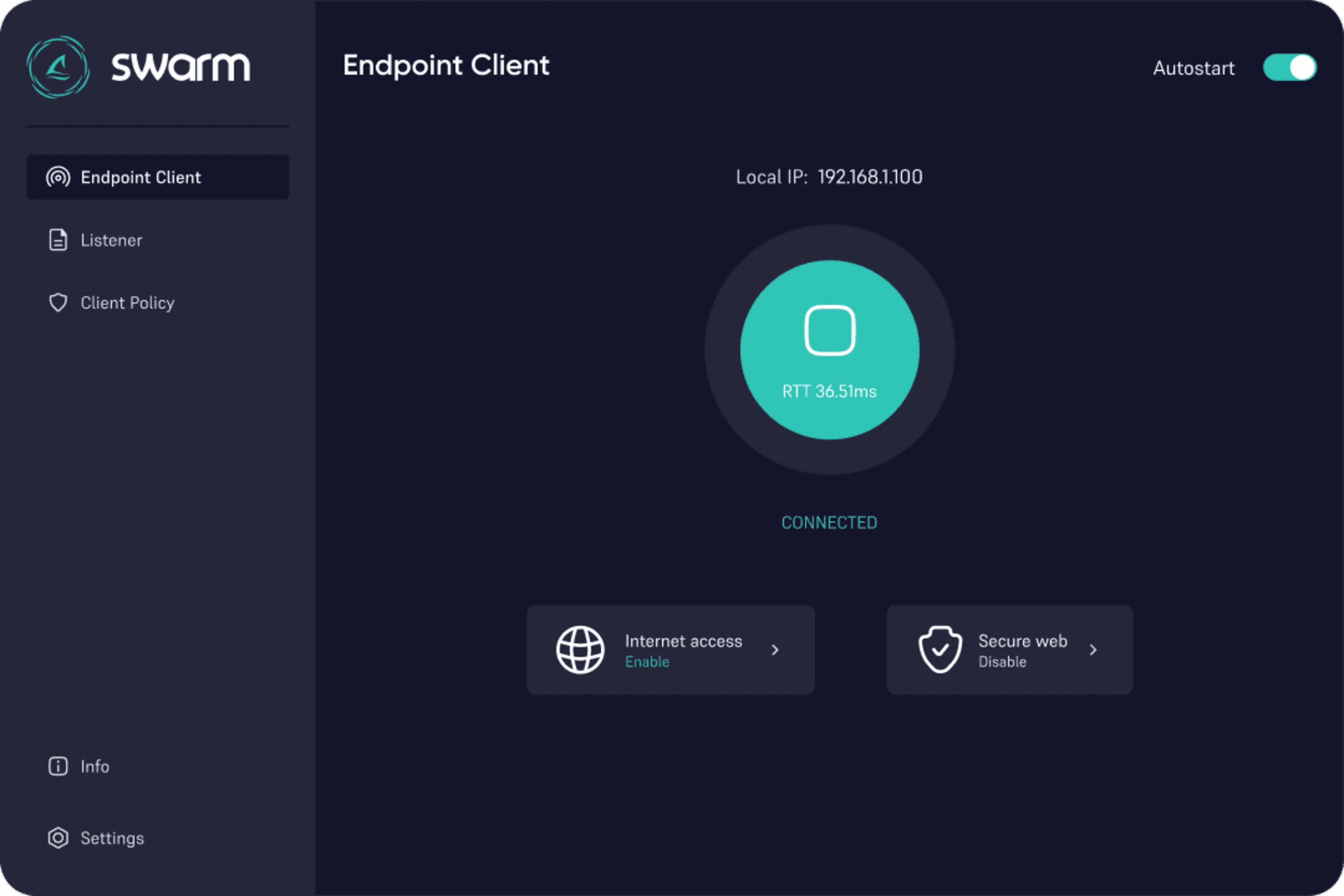
dynexo Secure Access uses an overlay transport that wraps all communications in a secure connection. In essence, it's a secure and adaptive solution for data transfer with the ability to increase complexity as needed
potential
Unlock the Power of Secure Business Connect

Highly adaptable to diverse business models
The system accommodates extra protocols, allowing users to customize complexity for high entropy without encryption.

Comply rigorous security standards
It incorporates well-known cryptographic protocols like AES-GCM, SHA-256, ECDHE, and Blake3 for encryption and authentication

Implementing comprehensive measures
Using the transport layer supports both TCP and UDP for data exchange
Unique in the world that the transport layer allows Secure Business Connect data with a complexity
connections
domains
endpoints
Benefits
Highlighting the Advantages of Secure Business Connect
Through our integrated portal, organizations can effortlessly establish, refine, and implement access policies
Save Cost
An innovative and cost-efficient strategy that replaces the need for hefty investments in high bandwidth, performance, and competitive SLAs during private connection deployments and upgrades, effectively minimizing both CAPEX, OPEX, and sunk costs.
Safer and Faster
Identity-based Zero Trust network access may block attacks against network infrastructure and prevent malicious activity.
Streamlined Implementation
Empower organizations to establish, fine-tune, and enforce access policies seamlessly across all locations, users, devices, and applications through a unified portal.
Global Distribution
Ensures user security regardless of location. Providing seamless access to apps and resources for devices and remote systems at all times and from any location.
How does Secure Business Connect work?
Overlay Transport
It packages all communications in a secure connection. Instead of directly packaging the network packets, only the data packets from the applications are packaged. The communication is therefore always "decoupled".

01
Controller
All endpoints register with the controller to receive the respective policies and connection information. The provisioning process, which is the initial setup of new clients and agents, also takes place through the controller.
02
Broker
The Broker acts as an intermediary between clients, agents, and relays. It ensures that all components can identify and locate each other. However, the Broker does not play a role in the actual data communication.
03
Relay
The development process drew from extensive experience in Asynchronous Transfer Mode (ATM) and mobile network design. The focus lies on mediating and forwarding data.
04
Client
For deployment on gateways and servers, the Client is also available in an embedded variant. The client is available in both light and dark modes, and it starts automatically with the operating system.
05
Agent
It also supports deployment on embedded systems. The control and management of the agent are done through the Admin Dashboard of the assigned controller.
Secure Business Connect Exchange
Elevating Security with TLS and Ulu-Cloud Intelligence
Communications ALWAYS occur from a client (Left) via the relay (Middle) to an agent (Right). Thanks to the identification features of each connection, the relay and agent know at all times which client is currently being used with which application and by which user.

Endpoint Profiling
Each client applies active endpoint profiling to identify the specific endpoint. All personal information remains on the end device and is only included in a cryptographically secure hash as part of the endpoint profiling result.

Policy
Attribute-based Policy
Secure Business Connect uses attributes to authorize communication. All required attributes are automatically defined by the engine and transmitted with each request by the client. Communication guidelines are at the heart of the Zero Trust Policy. Communication policies are implemented as allow policies. Similar to a firewall policy, the swarm engine selects the policies from top to bottom. Sources (Source) and destinations (Destination) can contain different object types. The object types are set automatically depending on the communication by the client and can be called up for each request. In the case of the agent, they are predefined by the policy engine.

Policy Object
Application
Applications are represented as application objects. These are clearly defined and can be reused seamlessly. They are firmly defined and can be reused directly.

Policy Object
Application Profiles
Application profiles offer additional features as policy options. Currently, the supported features are bandwidth in megabits (Mbps) and latency in milliseconds (ms).

Policy
Principle of the Security Architecture
In this technical journey, dynexo delve into the intricate details of designing, implementing, and maintaining a secure framework to protect your business from the ever-evolving threat landscape. Join us as we navigate the intricacies of security architecture to fortify your organization's digital fortresses.

Endpoint
An end device or workstation, such as a PC, laptop or mobile device
Domain
A domain represents a group of secure Business Connect endpoints that share a common characteristic. This can be an application, a special role, a specific scenario or a business case. In a domain, these endpoints, i.e. clients and agents, are
Client
A client or swarmer that is on the send side (left) of a communication.
Agent
A agent or worker located on the receive side (right) of a communication.
Application
An application or service that is to be made available within the domain.
Secure Access Packages
Secure Business Connect Bundles: Ensuring Security and Optimal Convenience
Access package 1
Divided
Virtual platform
2 domains and 50 endpoints
Shared bandwidth
Shared system resources
JSON log export to a destination
Access package 2
Guaranteed
Virtual platform
10 domains and 150 endpoints
Independent entity
Guaranteed bandwidth
Guaranteed resources
Log export to 2 destinations
Access package 3
Exclusive
Dedicated platform
50 domains and 500 endpoints
Independent entity
Any log exports
Also as an on-premise option